by Ravie Lakshmanan at The Hacker News
It didn’t take long. Intelligence agencies and cybersecurity researchers had been warning that unpatched Exchange Servers could open the pathway for ransomware infections in the wake of swift escalation of the attacks since last week.
Now it appears that threat actors have caught up.
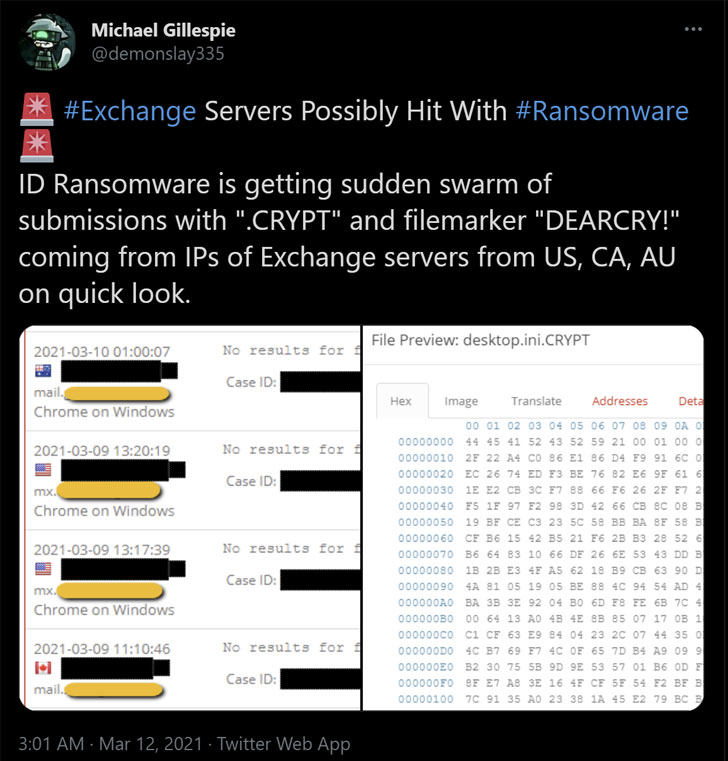
According to the latest reports, cybercriminals are leveraging the heavily exploited ProxyLogon Exchange Server flaws to install a new strain of ransomware called “DearCry.”
“Microsoft observed a new family of human operated ransomware attack customers – detected as Ransom:Win32/DoejoCrypt.A,” Microsoft researcher Phillip Misner tweeted. “Human operated ransomware attacks are utilizing the Microsoft Exchange vulnerabilities to exploit customers.”
Security firm Kryptos Logic said it identified about 6,970 exposed web shells, some of which were used to infect the compromised servers with DearCry ransomware, suggesting that other cybercriminal groups are piggybacking on the first-stage web shell backdoor planted by the Hafnium threat actor to install additional malware of their choice.
Calling DearCry a “copy” ransomware, Sophos Director Mark Loman said the strain creates encrypted copies of the attacked files using an encryption key embedded in the ransomware binary and deletes the original versions, thereby allowing the victims to “potentially recover some data” due to this encryption-behavior.
“Defenders should take urgent steps to install Microsoft’s patches to prevent exploitation of their Microsoft Exchange patches. If this is not possible, the server should be disconnected from the internet or closely monitored by a threat response team,” Loman said…
Continue Reading