by Ravie Lakshmanan at The Hacker News
Cybersecurity researchers have discovered a new malware dropper contained in as many as 9 Android apps distributed via Google Play Store that deploys a second stage malware capable of gaining intrusive access to the financial accounts of victims as well as full control of their devices.
“This dropper, dubbed Clast82, utilizes a series of techniques to avoid detection by Google Play Protect detection, completes the evaluation period successfully, and changes the payload dropped from a non-malicious payload to the AlienBot Banker and MRAT,” Check Point researchers Aviran Hazum, Bohdan Melnykov, and Israel Wernik said in a write-up published today.
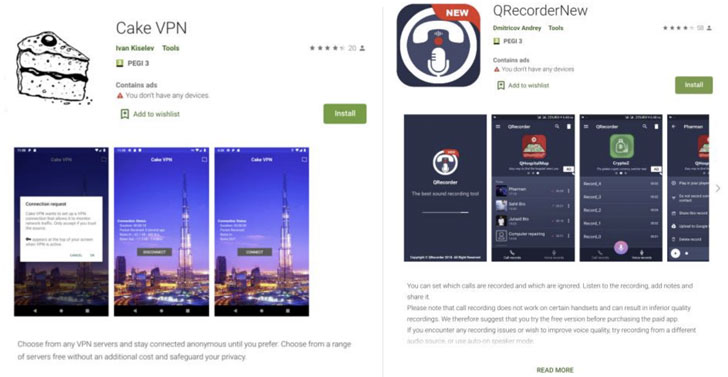
The apps that were used for the campaign include Cake VPN, Pacific VPN, eVPN, BeatPlayer, QR/Barcode Scanner MAX, Music Player, tooltipnatorlibrary, and QRecorder. After the findings were reported to Google on January 28, the rogue apps were removed from the Play Store on February 9.
Equally popular are other methods like versioning, which refers to uploading a clean version of the app to the Play Store to build trust among users and then sneakily adding unwanted code at a later stage via app updates, and incorporating time-based delays to trigger the malicious functionality in an attempt to evade detection by Google.
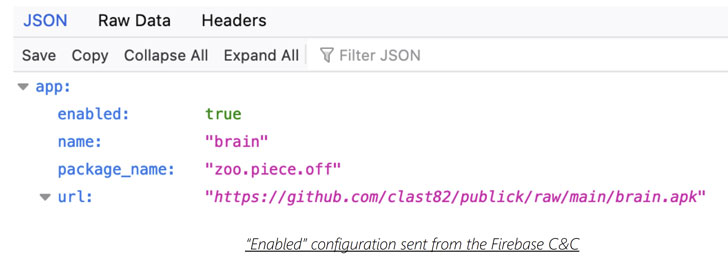
Clast82 is no different in that it utilizes Firebase as a platform for command-and-control (C2) communication and makes use of GitHub to download the malicious payloads, in addition to leveraging legitimate and known open-source Android applications to insert the Dropper functionality.
“For each application, the actor created a new developer user for the Google Play store, along with a repository on the actor’s GitHub account, thus allowing the actor to distribute different payloads to devices that were infected by each malicious application,” the researchers noted.
For instance, the malicious Cake VPN app was found to be based on…
Continue Reading